Achilles tested. Achilles certified.
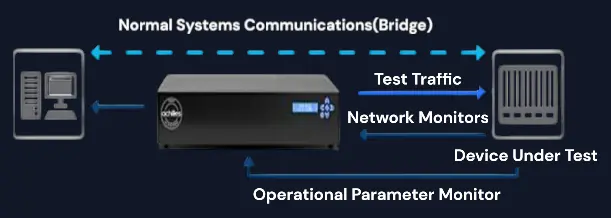

The Achilles Test Platform (ATP) is a specialized testing framework designed to enhance the security and durability of industrial automation and control systems. By simulating various operational challenges and cyber threats, ATP helps detect vulnerabilities, improve system resilience, and ensure compliance with industry regulations. It enables manufacturers and operators to proactively safeguard their infrastructure against potential risks, ensuring long-term reliability and performance. Achilles has the most extensive set of control protocol coverage, with tests designed specifically for devices found in critical infrastructure. The monitoring techniques also provide unparalleled visibility into your device's core functionality, enabling real-time analysis of data flow, network communication, and system responses. It continuously tracks all key operating parameters, including latency, packet integrity, protocol compliance, and fault tolerance during testing.

The Achilles Test Platform (ATP) is a specialized testing framework designed to enhance the security and durability of industrial automation and control systems. By simulating various operational challenges and cyber threats, ATP helps detect vulnerabilities, improve system resilience, and ensure compliance with industry regulations. It enables manufacturers and operators to proactively safeguard their infrastructure against potential risks, ensuring long-term reliability and performance. Achilles has the most extensive set of control protocol coverage, with tests designed specifically for devices found in critical infrastructure. The monitoring techniques also provide unparalleled visibility into your device's core functionality, enabling real-time analysis of data flow, network communication, and system responses. It continuously tracks all key operating parameters, including latency, packet integrity, protocol compliance, and fault tolerance during testing.

Real-world test environment monitoring
The patented test framework is specifically designed to allow you to test and monitor your device's capability under real-world conditions— allowing you to accurately verify and validate performance. The monitoring techniques also provide unparalleled visibility into your device's core functionality and monitor all key operating parameters during testing.
The monitoring techniques also provide unparalleled visibility into your device's core functionality, enabling real-time analysis of data flow, network communication, and system responses. It continuously tracks all key operating parameters, including latency, packet integrity, protocol compliance, and fault tolerance durng testing.
Comprehensive testing of industrial control specific protocols
Achilles has the most extensive set of control protocol
coverage, with tests designed specifically for devices found in critical infrastructure. Our experience with manufacturers and operators has allowed for tests that specifically address real-life scenarios in the field. The platform supports a wide range of industrial communication protocols, including Modbus, DNP3, IEC 61850, OPC UA, PROFINET, Ethernet/IP, and many others. These tests help identify vulnerabilities in protocol implementations, ensuring that devices can withstand cyber threats, unexpected network conditions, and operational stress without compromising performance.
Comprehensive testing of industrial control specific protocols
Achilles has the most extensive set of control protocol
coverage, with tests designed specifically for devices found in critical infrastructure. Our experience with manufacturers and operators has allowed for tests that specifically address real-life scenarios in the field. The platform supports a wide range of industrial communication protocols, including Modbus, DNP3, IEC 61850, OPC UA, PROFINET, Ethernet/IP, and many others. These tests help identify vulnerabilities in protocol implementations, ensuring that devices can withstand cyber threats, unexpected network conditions, and operational stress without compromising performance.
Fast, efficient, and easy automated testing methodology
Achilles manages the sending and monitoring of multiple tests and test sequences, resulting in the fast execution of a comprehensive suite of tests. It can complete a full set of tests for Achilles Communications Certification Level 1 in just 2 hours.
Fast, efficient, and easy automated testing methodology
Achilles manages the sending and monitoring of multiple tests and test sequences, resulting in the fast execution of a comprehensive suite of tests. It can complete a full set of tests for Achilles Communications Certification Level 1 in just 2 hours.
Extensive summary and detailed reporting
Detailed fault reporting allows you to identify and drill down on specific faults as well as easily share information across your organization. Through packet capture and reports, you can quickly reproduce faults and export regression test suite for other platform users to utilize. These reports can be exported into cxv, xml, and pdf files.
Use Cases
Automated QA Testing
The cost of correcting a vulnerability in the field is 65 times greater than if it is found and corrected during development.
Prepared products for certification
Test products in advance to ensure they will conform with industry recognized standards and certifications.
Communication Robustness Testing
Tests Communication robustness for industrial and automation devices,ensuring reliable data exchange under varying network conditions
Vulnerability Discovery Remediation
With extensive experience and deep industry knowledge, we provide insights and solutions that keep you ahead of the curve and other trends as well
Performance Availability Validation
Validates performance and availability based on specifications, ensuring consistent operation under different load conditions.
Fault Reproduction & Identification
Allows faults to be reproduced, isolated, and identified, enabling quicker troubleshooting and system reliability improvements.
Test Summary
Port Scanning is one of the first steps an attacker uses to gather information about a system to exploit it and ensuring consistent operation under different load conditions.
Storms: The ability of a device to handle packets varies with packet rate, Achilles can run this test with varying rate limits to determine the maximum value the device under test can handle.
Fuzzers: Fuzzers use random number generation to send invalid packets to test the behavior of the device under test.
Similar to known vulnerabilities, the grammars generate fuzzed versions of a known vulnerability, or traffic that almost triggers the vulnerability
Similar to known vulnerabilities, the grammars generate fuzzed versions of a known vulnerability, or traffic that almost triggers the vulnerability
Damaged packets are sent with small variations in packets such as mismatch in field length.
Protocol Summary
Protocols | Expanded | Stack |
Ethernet | Ethernet | TCP/IP |
ARP | Address Resolution | TCP/IP |
LLDP | Link Layer Discovery | TCP/IP |
IP V4 | Internet Version 4 | TCP/IP |
ICMP | Internet Control message | TCP/IP |
IGMP | Internet Group Message | TCP/IP |
TCP | Transmission Control Protocol | TCP/IP |
UDP | User Datagram Protocol | TCP/IP |
FTP | File Transfer Protocol | IT Protocol |
HTTP | Hyper text transfer Protocol | IT Protocol |
NTP | Network Time Protocol | IT Protocol |
RDP | Remote Desktop Protocol | IT Protocol |
RPC | Remote Procedure Call | IT Protocol |
Telnet | Telnet | IT Protocol |
DNP3 | Distributed Network Protocol | Control Protocol |
Ethernet/IP | Ethernet Industrial Protocol | Control Protocol |
GOOSE | Generic Object-Oriented | Control Protocol |
MMS | Manufacturing Message Specification | Control Protocol |
PROFINET | Process Field Network | Control Protocol |
ARINC | Aeronautical Ratio Incorporated | Aviation Protocol |
Zigbee | Zigbee Wireless Mesh | Wireless Protocol |
SES-92 | Serial Protocol | Serial Protocol |
Protocol Summary
Ethernet | Ethernet | TCP/IP |
ARP | Address Resolution | TCP/IP |
LLDP | Link Layer Protocol | TCP/IP |
IP V4 | Internet Protocol 4 | TCP/IP |
ICMP | Internet Control Message | TCP/IP |
IGMP | Internet Group Message | TCP/IP |
TCP | Transmission Control Protocol | TCP/IP |
UDP | User Datagram Protocol | TCP/IP |
HTTP Hyper Text Transfer IT Protocol
NTP Network Time Protocol IT Protocol
RPC Remote Procedure Call IT Protocol
RDP Remote Desktop Protocol IT Protocol
Telnet Telnet IT Protocol
E/IP Industrial Protocol Control Protocol
GOOSE Generic Object-Oriented Control Protocol
IEC104 Internet Commission Control Protocol
MMS Manufacturing Control Protocol
OPC/UA Open Communication Control Protocol
PROFINET Process Network Control Protocol
Zigbee Wireless Mesh Wireless Protocol
SES-92 Serial Protocol Serial Protocol
Test Summary
Port Scanning is one of the first steps an attacker uses to gather information about a system to exploit it and ensuring consistent operation under different load conditions.
Storms: The ability of a device to handle packets varies with packet rate, Achilles can run this test with varying rate limits to determine the maximum value the device under test can handle.
Fuzzers: Fuzzers use random number generation to send invalid packets to test the behavior of the device under test.
Similar to known vulnerabilities, the grammars generate fuzzed versions of a known vulnerability, or traffic that almost triggers the vulnerability
Similar to known vulnerabilities, the grammars generate fuzzed versions of a known vulnerability, or traffic that almost triggers the vulnerability
Damaged packets are sent with small variations in packets such as mismatch in field length.
Protocol Summary
Protocol Summary
Ethernet | Ethernet | TCP/IP |
ARP | Address Resolution | TCP/IP |
LLDP | Link Layer Protocol | TCP/IP |
IP V4 | Internet Protocol 4 | TCP/IP |
ICMP | Internet Control Message | TCP/IP |
IGMP | Internet Group Message | TCP/IP |
TCP | Transmission Control Protocol | TCP/IP |
UDP | User Datagram Protocol | TCP/IP |
HTTP Hyper Text Transfer IT Protocol
NTP Network Time Protocol IT Protocol
RPC Remote Procedure Call IT Protocol
RDP Remote Desktop Protocol IT Protocol
Telnet Telnet IT Protocol
E/IP Industrial Protocol Control Protocol
GOOSE Generic Object-Oriented Control Protocol
IEC104 Internet Commission Control Protocol
MMS Manufacturing Control Protocol
OPC/UA Open Communication Control Protocol
PROFINET Process Network Control Protocol
Zigbee Wireless Mesh Wireless Protocol
SES-92 Serial Protocol Serial Protocol


